The Invisible Threat: Unmasking Internet Frauds and
Cybersecurity
Technology
Published on 08-09-2023

These activities include offenses like identity theft, phishing, and other hacking techniques intended to defraud people of their money. Internet scams, which target victims through online services, generate millions of rupees in fraudulent activity annually. Furthermore, these figures continue to climb as internet usage expands and cybercriminal tactics become increasingly sophisticated.
Internet fraud can be broken down into several key types of attacks, including:
- Phishing and spoofing: Phishing and spoofing involve using email and online messaging services to deceive victims into divulging personal information, login credentials, and financial details.
- Data breach: Data breach encompasses illicitly acquiring confidential, protected, or sensitive data from a secure location and transferring it to an untrusted environment. This includes the unauthorized theft of data from both users and organizations.
- Denial of service (DoS): Denial of service (DoS) pertains to disrupting access to online services, systems, or networks for malicious purposes.
- Malware: Malware refers to the deployment of malicious software with the intent of causing harm or disabling users’ devices while also stealing personal and sensitive data.
- Ransomware: Ransomware is a subtype of malware that restricts users from accessing critical data and subsequently demands payment in exchange for the promise of restoring access. Typically, ransomware is delivered through phishing attacks.
- Business email compromise (BEC): Business email compromise (BEC) represents a sophisticated attack targeting businesses that frequently use wire payments. It compromises legitimate email accounts through social engineering techniques to initiate unauthorized charges.
Now let us gain some knowledge about the various types of internet fraud:
Cybercriminals employ multiple attack vectors and strategies to perpetrate internet fraud. These methods include malicious software, email, instant messaging services for disseminating malware, forged websites designed to steal user data, and intricate, widespread phishing schemes.
Need HELP?
Consult with Expert Now
- Spoofing: Spoofing is a form of attack on a computer device in which the perpetrator attempts to steal the legitimate user's identity and masquerade as someone else. Such attacks are executed to compromise system security or steal user information.
- Phishing: Phishing is a computer device attack in which the assailant seeks to illicitly obtain sensitive user information through electronic communication, masquerading as a trusted organization, often in an automated manner, with fraudulent intent.

Email-based phishing scams represent one of the most prevalent forms of Internet fraud, which presents a significant threat to Internet users and businesses.
In email phishing scams, cybercriminals impersonate individuals known to their victims or those considered reputable. These attacks aim to entice individuals into clicking on a link leading to a malicious or forged website designed to mimic a legitimate one or open an attachment containing harmful content.
Initially, the hacker compromises a legitimate website or creates a fraudulent one. Subsequently, they obtain a list of email addresses to target and distribute an email message designed to deceive recipients into clicking a link directing them to the deceptive website.
When a victim clicks on the link, they are redirected to the counterfeit website, which may prompt them to provide a username and password or automatically download malware onto their device. This malware is then used to steal data and login credentials.
The hacker can leverage this information to access the user’s online accounts, pilfer additional data such as credit card details, infiltrate corporate networks linked to the device, or engage in broader identity fraud.
Email phishing scammers often emphasize the need for immediate action, coercing victims by claiming their online accounts or credit cards are at risk and urging them to log in promptly to resolve the issue.

Many internet fraud schemes exploit popular events celebrated by people, including birthdays, Christmas, and Easter, often marked by exchanging greeting cards via email. Hackers typically use this by embedding malicious software within email greeting cards.
When recipients open these cards, the malware is downloaded and installed on their devices.
The consequences of such actions can be severe. Malware may lead to bothersome pop-up ads that disrupt application performance and slow the device. A more alarming outcome is the theft of the victim’s personal and financial information, along with their computer being employed as part of a widespread network of compromised computers, a botnet.
Credit card fraud typically occurs when hackers illegitimately obtain individuals’ credit or debit card information to steal funds or make unauthorized purchases.
To acquire these details, internet fraudsters frequently entice victims with seemingly irresistible credit card or bank loan offers. For instance, a victim may receive a message from their bank asserting that they qualify for a particular loan offer or that a substantial amount of money is accessible to them as a loan. Despite widespread awareness that such proposals are usually too good to be true, these scams persistently deceive individuals.
While there are various methods through which scammers attempt to deceive individuals and gain access to their funds, one of the most prevalent tactics involves phishing SMS messages. Phishing attempts via SMS are a global issue where cybercriminals aim to trick people into divulging sensitive information.
These scams often involve impersonating banks and creating a sense of urgency by claiming recipients’ bank accounts are in jeopardy. Victims are then asked to update their KYC or PAN information by clicking on a link provided in the SMS.
Phishing SMS fraud is very common, and many banks have released an advisory for people not to believe in such SMS. Once someone falls victim to these fraudulent SMS messages and clicks on the link, scammers can gain unauthorized access to their mobile devices or banking credentials, resulting in financial losses.
Recognizing that legitimate financial institutions worldwide will never request sensitive information through unsolicited messages is crucial. Therefore, it’s imperative to exercise caution and never respond to suspicious SMS messages or unsolicited requests for personal data. Above all, refrain from sharing sensitive information such as account numbers, card details, OTPs, CVV codes, or personal identification.

Another type of Phishing is Voice Phishing or fake voice call scam. Fraudsters employ sophisticated AI technology to produce counterfeit voice calls that closely mimic genuine interactions, deceiving individuals into providing money.
Some precautions on how to be safe from Phone call scams
To ensure your safety and that of your loved ones in the face of AI voice scams, it’s essential to exercise caution and take proactive steps. Here are some vital guidelines to bear in mind when dealing with suspicious calls:
- Verify Callers: Prioritize verifying the caller’s identity by employing a codeword or posing a question only they would know.
- Utilize Identity and Privacy Protection Services: Request the caller to confirm their identity using a secret word or by responding to a personal question.
- Ignore Unknown Calls: When an unfamiliar caller’s number appears, allow it to go to voicemail. If they leave a message, cross-verify their number with the official website associated with the entity they claim to represent.
- Refrain from Clicking Links in Texts: Avoid clicking on links sent via text messages, as they may contain malware or redirect you to counterfeit websites.
- Do Not Share OTP: Never disclose any financial or personal information to individuals who contact you via phone or text. Such individuals may be scammers attempting to extract your passwords, bank details, or credit card numbers.
- Decline Remote Access: Do not grant anyone remote access to your device. Remote access could lead to malware installation or data theft.
- Exercise Caution with Caller ID: Be skeptical of caller ID information, as scammers can manipulate it to disguise their true identities.
- Terminate Suspicious Calls: Do not hesitate to hang up in the face of unusual or pressing demands from callers. End the call and avoid engaging with unfamiliar numbers.
A data breach is an incident that exposes confidential, private, protected, or sensitive information to an unauthorized person.
It can occur as a consequence of an unintentional event or a deliberate action aimed at acquiring information from an individual or an organization. For instance, an employee may inadvertently disclose sensitive data or intentionally pilfer company information to share with or sell to a third party. Alternatively, a hacker might infiltrate a corporate database containing sensitive information.
Regardless of the underlying cause of a data breach, the stolen information can be leveraged by cybercriminals to generate profits by selling the data or incorporating it into broader cyberattacks. Typically, a data breach involves compromising or stealing information such as bank account details, credit card numbers, personal health records, and login credentials for email accounts and social networking platforms.
Data breaches can result from external attackers targeting an organization or multiple organizations for specific data types, or individuals within an organization can instigate them. Hackers often employ targeted cyberattacks against particular individuals.
To protect themselves from data breaches, organizations and employees must implement the following ways:
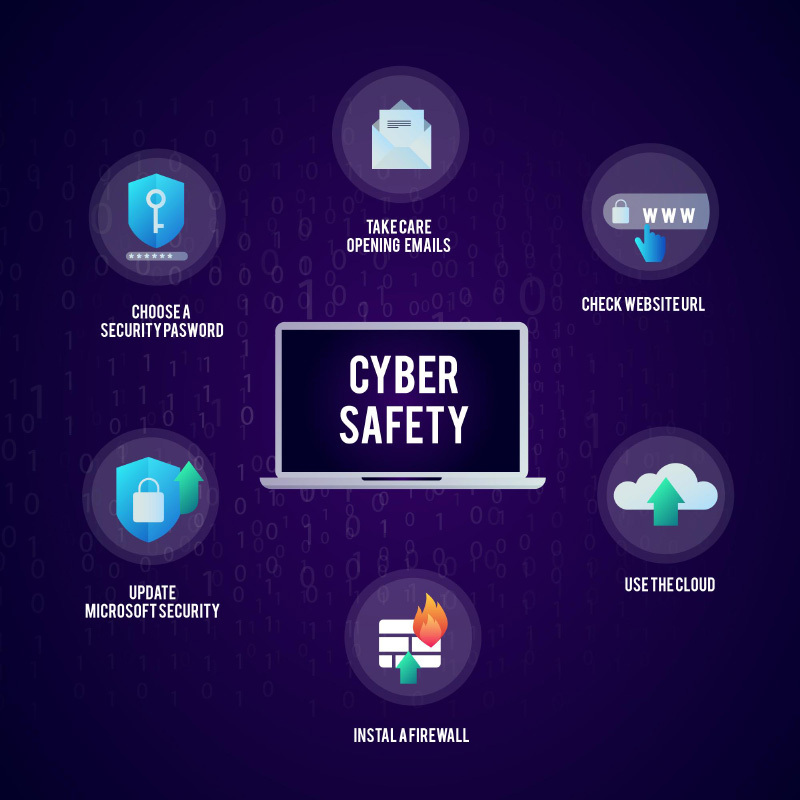
- Utilize Strong Passwords: Weak passwords remain the primary cause of data breaches, providing attackers a gateway to steal user credentials and gain unauthorized access to corporate networks.
- Implement Multi-Factor Authentication (MFA): In recognition of the inherent limitations of passwords, individuals and organizations should never solely rely on passwords for security. MFA mandates that users validate their identity beyond simply entering a username and password.
- Keep Software Current: Continuously utilize the latest versions of software systems to pre-empt potential exploits stemming from vulnerabilities. Activate automatic software updates whenever feasible and consistently follow through with updates and patches as prompted.

- Prioritize Secure URLs: Users should exclusively interact with Uniform Resource Locators (URLs) that exhibit secure characteristics. Secure URLs typically commence with “Hypertext Transfer Protocol Secure” (HTTPS). Additionally, it’s imperative to access trusted URLs exclusively. Generally, exercise caution when clicking on any links within email messages.
- Educate and Train Employees: Organizations are responsible for educating employees about online risks, familiarizing them with common cyberattack types, and equipping them with the skills to identify potential threats.
- Develop an Incident Response Plan: Given the increasing sophistication of cybercriminals and the rising prevalence of cyberattacks, businesses must formulate a comprehensive response plan for worst-case scenarios. This plan should outline the designated individual responsible for reporting the attack to relevant authorities and provide a clear roadmap for subsequent actions.

DENIAL OF SERVICE (DOS)
A Denial-of-Service (DoS) attack is a deliberate assault to render a machine or network inoperative, rendering it inaccessible to its intended users. These attacks achieve their objective by inundating the target with an overwhelming volume of traffic or by dispatching information designed to trigger system failure. In both scenarios, the DoS attack disrupts the provision of services or resources that legitimate users anticipate receiving, such as employees, members, or account holders.
Typically, the targets of DoS attacks include web servers of prominent organizations, including those in the banking, commerce, media, government, and trade sectors. While DoS attacks generally do not lead to the theft or compromise of substantial information or assets, they can impose significant costs on victims regarding the time and financial resources required for mitigation.
Malware refers to software intentionally crafted for either stealing data or causing harm to computer or software systems. It encompasses various malevolent software forms, including viruses, spyware, and ransomware. Cybercriminals employ these malicious tools to breach network security and compromise devices, ultimately leading to data theft or system disruption.
Different types of malware threats impact online networks or attached devices:
- Viruses: These malicious programs attach themselves to clean code, spread rapidly, and disrupt system functionality, often concealed within executable files.
- Worms: Worms propagate through networks by connecting with multiple machines, potentially infecting entire networks if not halted.
- Trojan Viruses: Named after the deceptive Trojan horse, these appear as legitimate software but create backdoors for other malicious software to gain unauthorized access.
- Spyware: Operating covertly, spyware secretly monitors user activity, collecting sensitive information like credit card details and passwords.
- Ransomware: Ransomware locks computers or networks, demanding payment to release access and providing decryption keys upon payment.
- Adware: Adware inundates users with unwanted advertisements, often disguised as innocent ads or bundled with seemingly harmless software.
- Rootkit: Rootkits grant attackers administrator-level privileges while remaining hidden, enabling unauthorized access and system changes.
- Keyloggers: Keyloggers record keystrokes, enabling attackers to obtain passwords, usernames, and payment details.
- Crypto-jacking: Attackers exploit target devices to mine cryptocurrencies, harnessing their computing power for digital currency generation.
- Rogue Software: Rogue software masquerades as malware removal tools, tricking users into installing and paying for actual malware.
- Scareware: Scareware employs psychological tactics to deceive users into purchasing unnecessary and potentially harmful software by falsely portraying security threats.
- Back up your data
- Educate employees on signs of malware and how to avoid it.
- Check for vulnerabilities to avoid malware entering the network.
- Using firewall protection.
Detect malware with antivirus.
BEC is a type of email phishing that targets senior executives and finance department staff.
The individual orchestrating the malicious attack assumes the identity of a person vested with decision-making power, often someone capable of authorizing financial transactions, granting system entry, or divulging sensitive information.

BEC scams aim to create an appearance of legitimacy, but upon closer examination, you may notice the following unmistakable indicators:
- Spelling or grammatical anomalies: Hackers, relying on limited information, may introduce peculiarities like using your full name instead of a familiar nickname or employing a generic greeting with no personalization. Additionally, since hackers aren’t industry experts, you may encounter grammar, spelling, or other errors uncommon in your organization.
- Irregularities in the sender’s address format or spelling: When unable to use a genuine email address, hackers may construct one that mimics authenticity. Keep an eye out for missing letters, dashes instead of underscores, and special characters closely resembling letters of the alphabet, among other discrepancies.
- Unusual or atypical requests: Hackers may attempt to justify an unusual or out-of-the-ordinary request by framing it as a particular circumstance, an urgent favor, or a mandatory requirement. If a request appears unconventional, delving deeper to confirm its authenticity is prudent.
To safeguard themselves and evade falling victim to phishing schemes, internet users should maintain a vigilant stance towards the common forms of internet fraud.
It is imperative never to transfer money to individuals encountered online, refrain from disclosing personal or financial information to unverified or untrustworthy sources, and exercise caution when experiencing email or instant message hyperlinks or attachments. In the event of being targeted, individuals should promptly notify authorities about online scammer activities and report phishing emails.
Mitigating credit card fraud entails vigilant monitoring of bank accounts, setting up credit card activity alerts, enrolling in credit monitoring services, and leveraging consumer protection resources. In case of credit card fraud, users should promptly report the incident to pertinent legal authorities and credit reporting agencies.













